- SnapLogic - Integration Nation
- Designing and Running Pipelines
- Passing Body Content in Post Snap
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Passing Body Content in Post Snap
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-09-2022 11:43 AM
Hi,
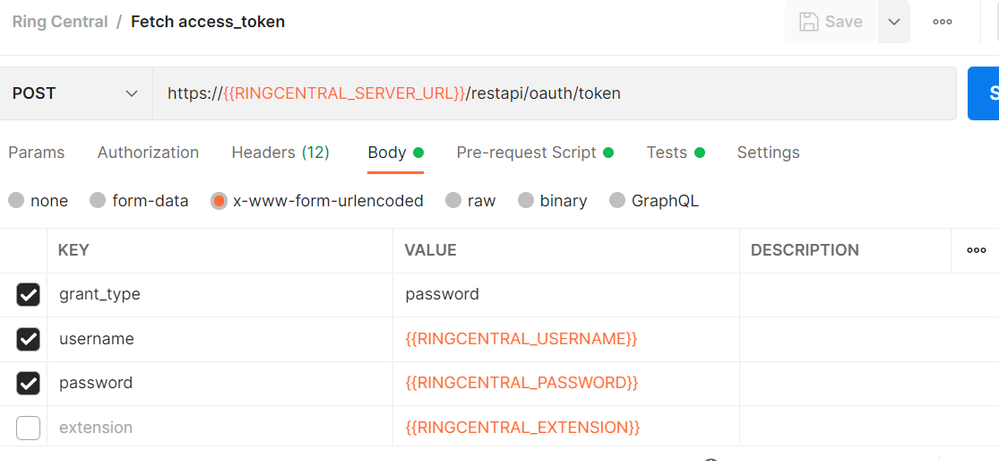
This is a very novice question, but I am having trouble with a post request snap. This is just to authenticate with the RingCentral platform to receive a token for API consumption. I am able to successfully retrieve an access token when calling the oauth/token endpoint in Postman. The issue arises when I try to move this post call into SnapLogic. The call requires certain parameters to be passed through the body and I am not sure how to duplicate this in SnapLogic post snap. Please see the screenshot of the Postman call Body tab below.
I have created a basic account in SnapLogic to store the username and password and my post snap references that account. I am also aware that the credentials of a basic account can be accessed using the “Account.Username” and Account.Password" of the respective referenced account within the snap.
I am just not sure how to build out the body section in the “x-www-form-urlencoded” format as shown in the screenshot? The error I get back when validating this post snap is just a 400: Bad Request.
Any insight/help that anyone could provide would be greatly appreciated. Please let me know if additional information is needed to provide assistance.
Thanks,
James
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-17-2022 12:48 PM
Because I chose password for the grant_type, I did not check the auto refresh token option. Could that be the reason I see 401 errors on the RingCentral side? It looks like the it retries 3 times on the SnapLogic side. So could it be the 401 is being thrown because it tries to use the token it already has, but it is expired, so then requests a new token and all we see on the SnapLogic side is a successful run because after getting a new token on the 2nd try, everything works.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-17-2022 01:19 PM
you should have auto refresh enabled, it should still work with the password grant. You should still be getting a refresh token back from the request, you can confirm it with the account edit view, it should have Value is encrypted for the “Refresh token” like the below screenshot
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-18-2022 10:11 AM
Okay I enabled that yesterday afternoon. So far on the Ring Central side, the 401 errors have diminished. In fact today(03/18) there is a 100% success rate running that pipeline every 59 minutes.
This may be an obvious question and I think I know the answer, but just for clarification, with the auto refresh enabled does that enable a background process to run on the account to refresh the token at the needed interval to prevent the account from having an expired token (independent of the state of a specific pipeline that may utilize that account)?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-18-2022 10:40 AM
yes, the process looks for all OAuth accounts that are nearing expiration or expired, with a valid refresh token and does the authentication token refresh. It does periodic checking and looks for tokens that will expire before the next check of expired tokens and will refresh all of those tokens accordingly. In the case of your situation, if it doesn’t refresh for 7 days (which is the max life of a refresh token) it would then have to start from the initial password token request.
- Truncation error with MS SQL Bulk Load snap, column reported not issue, which column is real issue? in Designing and Running Pipelines
- The "Pipeline execute" is changing data types? in Designing and Running Pipelines
- Parsing XML using a Python script returns an encoding error message in Designing and Running Pipelines
- Hyperlink URL Error in HTML/XML Generator in Designing and Running Pipelines
- PostgreSQL Bulk Upload in Designing and Running Pipelines