- SnapLogic - Integration Nation
- Patterns
- Re: Encrypt and decrypt sensitive data in a source
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Encrypt and decrypt sensitive data in a source
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-22-2018 02:10 PM
Created by @pavan
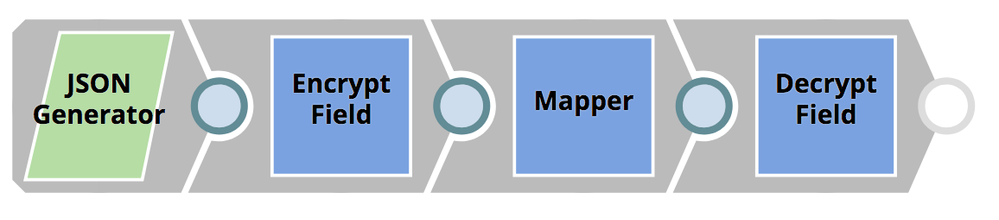
This pipeline pattern will encrypt fields passed as JSON docs using a defined transform type (AES), and decrypts and gives back the original message. This pattern is useful for encrypting sensitive messages (credit card info, SSN, patients name, DOB etc).
Configuration
Within the JSON Generator, replace “Enter certificate here” with your own certificate.
Sources: JSON
Targets: JSON
Snaps used: JSON Generator, Encrypt Field, Mapper, Decrypt Field
Downloads
Encrypt & Decrypt Fields.slp (9.1 KB)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-23-2018 03:31 PM
@pavan Once encrypted, do I need to pass all the information onward? Is it a security risk to do so?
ENC {
"transformation":"AES/CBC/PKCS5Padding",
"iv":"[MYIV]",
"type":"STRING",
"ciphertext":"[MYCIPHERTEXT==]",
"key_params": {
"passphrase": {
"key_gen_iterations":10000,
"key_gen_algorithm":"[ALGORITHM]",
"key_algorithm":"AES",
"key_salt":"[SALTKEY]",
"key_size":128
}
}
}:ENC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-23-2018 03:57 PM
Yes, the information is needed to correctly decrypt the ciphertext.
No, it’s okay to send the IV in the clear and the rest of the information is used to configure the decryption process.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-14-2019 11:21 PM
@tstack I have a similar scenario. Please read through the steps.
- We are using Encryption & Decryption in 2 seperate ultra pipelines, where first pipeline would encrypt the password field and send this data to second pipeline & the second pipeline would decrypt the data and use it.
- The problem is we are giving away key information like Type Of Algorithm, IV, Key_SALT over the internet along with the Ciphertext which is a security concern.
- Our design has to have 2 seperate ultra pipelines & not pipeline execute as its an architectural decision.
How can we achieve decrypting the field, without giving away these key attributes?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-15-2019 06:58 AM
These values are not secrets, so I don’t think there should be a problem.
Can I ask what is driving the decision to not use PipeExec?
- ZipFile Writer - Create a zip file without writing to SLDB in Snap Packs
- How to Decrypt fields for an entire table at once? in Designing and Running Pipelines
- Encrypt and decrypt of Field in Designing and Running Pipelines
- Encrypt and decrypt sensitive data in a source in Patterns
- DES encryption and decryption in SL in Designing and Running Pipelines